The Rise of Zero Trust Security
The traditional security model, based on implicit trust within the network perimeter, is becoming increasingly obsolete in the face of rapidly evolving cyber threats and the rise of remote work and hybrid environments. Zero Trust Security is emerging as a modern and effective approach, where no user or device is automatically trusted, even within the network. By enforcing systematic verification at every access attempt, it strengthens security while adapting to the needs of a decentralized IT infrastructure. This technology watch explores the rise of Zero Trust, its growing adoption, its impact on IT professionals, and the challenges of implementing it in businesses.
1.Why is Zero Trust Becoming Essential ?
With the rise of cyberattacks, the expansion of remote work, and the widespread adoption of hybrid environments (cloud, SaaS, BYOD), the traditional security model based on a trust perimeter is showing its limits. Ransomware attacks, account compromises, and lateral movements within internal networks demand a new approach: Zero Trust Security (ZTS).
Unlike traditional models that assume everything inside the network is trustworthy, Zero Trust adopts a continuous verification stance. Every user, device, and application must constantly prove their legitimacy before gaining access to resources.


The Rise of Cyberattacks
Ransomware and phishing attacks exploit the weaknesses of traditional security models.
The Rise of Remote Work and Cloud Computing
As IT infrastructures become increasingly distributed, perimeter-based security has become ineffective.
Regulations and Legal Requirements
Frameworks like the U.S. Cybersecurity Executive Order of 2021 mandate the implementation of Zero Trust within federal agencies.
Evolving Internal Threats
An increasing number of attacks originate from within the organization, whether by malicious employees or external actors who have gained legitimate access.
2.Trends and Adoption of Zero Trust
More and more companies and public organizations are adopting Zero Trust. According to a Gartner study, by 2025, 60% of enterprises will have implemented a Zero Trust strategy, compared to just 10% in 2020. This trend is being accelerated by several factors.
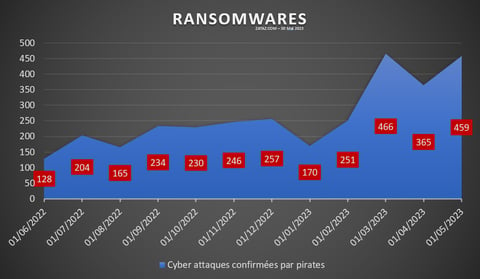






Zero Trust is evolving with increasingly advanced technologies.
Zero Trust Network Access (ZTNA)
It replaces traditional VPNs by securing access to resources based on the user's identity and context. Unlike VPNs, which provide broad access to the network, ZTNA enforces strict segmentation and conditional access to specific applications. Solutions like Zscaler Private Access, Palo Alto Prisma Access, and Netskope enable seamless implementation of this approach.
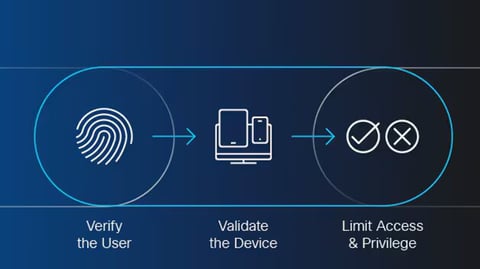
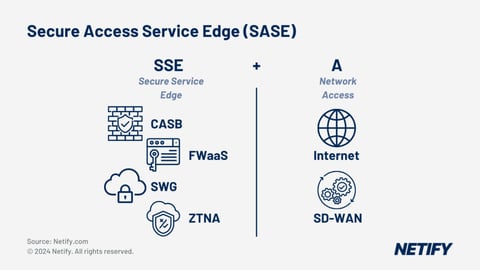
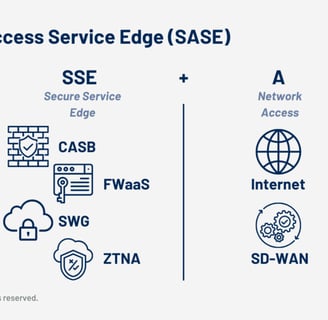
SASE (Secure Access Service Edge)
It merges the principles of Zero Trust with security and network management in a cloud-based model. SASE integrates features such as ZTNA, SWG (Secure Web Gateway), CASB (Cloud Access Security Broker), and SD-WAN, enabling secure and optimized connectivity regardless of user location.
AI-based Security and Machine Learning
Artificial intelligence enables the analysis of user behavior and the anticipation of threats in real-time.


Adaptive Security Posture
Access is granted or denied dynamically based on continuous risk analysis.


Contextual Access Management
Real-time signals (such as location, device type, and user behavior) are used to dynamically adjust permissions.


Adaptive Machine Learning
It enhances anomaly detection and automates incident response through advanced predictive models.


Passwordless Authentication
The use of biometrics, FIDO2 security keys, and cryptographic tokens eliminates the risks associated with passwords.

3.Principles and Implementation
Zero Trust is based on several fundamental concepts.
Systematic Verification: Every access attempt is controlled, whether it comes from inside or outside the network.
Principle of Least Privilege: Access to resources is reduced according to the precise needs of users.
Micro-Segmentation: Limiting lateral movements by segmenting critical resources.
Continuous Monitoring and Incident Response: Real-time behavior analysis to detect any suspicious activity.
Identity-Centric Security Approach: User identity and context are at the core of access decisions.
To implement Zero Trust, several key steps are essential :
Identifying critical resources and users who need access to them.
Implementing strong authentication (MFA, biometrics, Passkeys, FIDO2).
Micro-segmentation of access through solutions like Cisco, Palo Alto, or Zscaler.
Monitoring and behavioral analysis with SIEM and XDR tools (Microsoft Sentinel, Splunk, CrowdStrike).
Establishing an access compliance and governance policy to ensure continuous monitoring.
4.Impacts for IT Professionals
4.1 New Skills Required
Proficiency in IAM (Identity and Access Management) and MFA (Multi-Factor Authentication) solutions: IAM refers to the management of users' digital identities and their access to an organization's resources. MFA enhances security by requiring multiple identity verifications before granting access.
Knowledge of segmentation tools and ZTNA (Zero Trust Network Access): ZTNA solutions provide more granular access control to resources, relying on the user's identity and context, while network segmentation prevents lateral movements of attackers.
Security log management and analysis (SIEM, XDR): SIEM (Security Information and Event Management) collects and analyzes security events, while XDR (Extended Detection and Response) extends this monitoring across all levels of the network, endpoints, and cloud.
Understanding Zero Trust architectures and associated frameworks (NIST 800-207, Forrester ZTX): NIST 800-207 is a reference for implementing Zero Trust architectures, while Forrester ZTX expands these principles to include advanced tools such as AI.
4.2 Challenges and Resistance
Integration Complexity: Adapting existing systems to a Zero Trust model can be costly and requires a redesign of security policies. The transition can also be lengthy and challenging to implement in complex infrastructures.
Training and Awareness: Users need to be educated about the new security policies and changes in their user experience. Adopting Zero Trust requires a cultural shift in the organization's approach to security.
Regulatory Evolution: Companies must comply with new cybersecurity standards and ensure their implementation meets compliance requirements, such as ISO 27001 or the GDPR (General Data Protection Regulation).
4.3 Organizational Changes
Cross-Team Collaboration: Network, system, and security teams must work together to deploy and maintain an effective Zero Trust architecture. This requires enhanced cooperation to ensure consistent access management.
Security Culture Shift: Zero Trust requires a continuous security approach based on systematic verification, which necessitates an evolution in the company's security culture, with heightened vigilance against threats.


5. Use Cases and Feedback
Google and BeyondCorp
Google was one of the pioneers of Zero Trust with its BeyondCorp initiative, which eliminated traditional VPNs and secured access to its resources based on the principle of continuous verification.
Microsoft and his Zero Trust Adoption Framework
Microsoft integrates Zero Trust into its ecosystem through Azure AD Conditional Access, Defender for Identity, and Microsoft Sentinel, making adoption easier for businesses using its cloud solutions.




The U.S government
The U.S. government has mandated the adoption of Zero Trust across federal agencies as part of its 2021 cybersecurity executive order, aiming to strengthen security in response to evolving cyber threats.


Banks & Insurance Companies
Financial institutions are increasingly adopting Zero Trust to protect sensitive customer data and transactions, ensuring robust security measures against evolving threats such as cyberattacks and insider risks. By implementing Zero Trust, these organizations can enforce stricter access controls, monitor user behaviors, and secure critical assets in both on-premise and cloud environments.


6. Sources & References
Gartner – "The Future of Zero Trust Security" (2024)
NIST Special Publication 800-207 – "Zero Trust Architecture"
Microsoft Security Blog – "Zero Trust Adoption Framework"
Google BeyondCorp – "Implementing Zero Trust in Cloud Environments"
Rapport Forrester – "Zero Trust Market Trends 2024"
Cisco – "Zero Trust Security for Enterprise Networks"
Palo Alto Networks – "ZTNA vs VPN: The Future of Secure Access"
7. Conclusion
Zero Trust Security is emerging as a response to the challenges of modern cybersecurity. Its growing adoption and integration with innovative technologies make it a central topic for IT professionals. Transitioning to this model requires infrastructure and skillset adjustments, but it ensures enhanced protection against current and future cyber threats. Companies must start considering Zero Trust strategies now to ensure resilience against cyberattacks and anticipate future regulatory requirements.